
Due to constant digital and technological evolution, the importance of cyber security regarding knowledge and implementing effective solutions is extremely significant. Everyone wants to work from everywhere and most people want to work with devices they want, fit their own requirements, and maybe already own (BYOD). Applications are moving from on-premises private client / server infrastructure into the cloud and are accessible from everywhere for everyone (SaaS).
A variety of security architectures and models are currently available, focusing on different attacking scenarios, while even more are under development by paying attention to current research and technological trends.
One of the most widely used terms regarding security models, by focusing on the issue of trust, is the Zero Trust architecture. It is considered a highly strategic mechanism, supporting industries and organizations to continuously validate and verify digital processes and stages.
Moreover, due to the nature of Zero Trust about validation and verification of data and the actors participating in the corresponding interactions, there is an increased potential related to the compatibility of the model with SIEM solutions, since it is focused on threat detection and data management.
What is a Zero Trust Architecture?
Generally, the basis of the architecture is dedicated to the assumption of “never trust, always verify”. In that regard, the architecture is designed to verify every type of data collected, such as a stakeholder’s role in a specific process and location, ensuring the safety of their personal device, the request of certain data, etc.
A relative example of the Zero Trust architecture is the following:
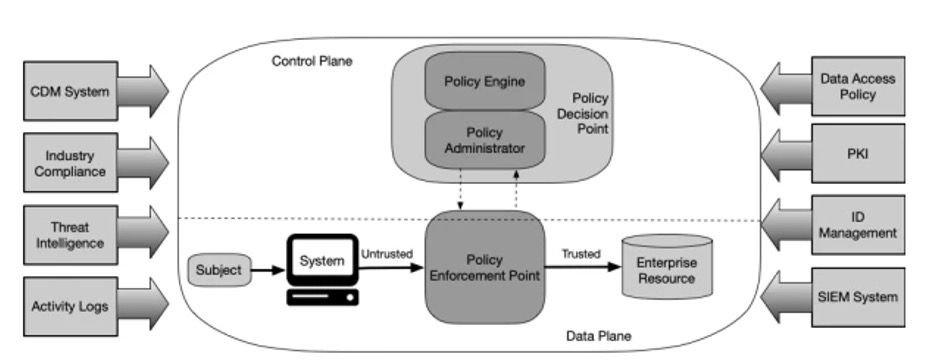
Depending on the organization’s infrastructure, the components of a Zero Trust model can be either cloud-based or on-premises. Also, it is not guaranteed that the architecture is a solid design that is simply implemented in an industry, but it is adapted according to certain goals and the overall existing framework for maximum efficiency and performance. Simultaneously, the model may need to be installed in smaller parts or stages of the infrastructure, rather than the whole organization.
For the sake of keeping this blog a summative review of the Zero Trust model, we are going to describe only the core components of the architecture:
Policy Engine (PE): Its purpose is to utilize decision-making algorithms, about permitting access to users or actors of the data interactions, depending on the feed and input provided by the surrounding data sources
Policy Administrator (PA): Depending on the final decision provided by PE, it either creates or declines a communication path between the organization’s system and the user requesting access.
Policy Enforcement Point (PEP): It acts as a monitoring component of the communication path. It is capable of maintaining or deactivating an active link by monitoring the interaction between the user and the central system
What are the Zero Trust model principles?
The motivation for implementing Zero Trust is heavily based on a variety of principles defined by the corresponding model. Some of them are presented below:
Constant Verification: As mentioned above, the basis of Zero Trust is “never trust, always verify”. The model is designed to assume that the presence of attackers inside or outside the organization’s system is highly possible. Therefore, implementations such as risk-based conditional access and dynamic policy employment ensure continuous verification due to the vast flow of data, workloads, and events.
Blast Radius Limitation: Zero Trust is capable of limiting access paths to the organization’s central systems, through real-time monitoring, during the presence of a threat or attacker, while giving time for defense systems to detect, analyze and block the attack.
Variety of protection mechanisms: Zero Trust is highly supportive of defense mechanisms. Some of the most known are multi-factor authentication for identity verification and granting access with at least two forms of evidence confirmation, limiting access for authenticated users for providing data access only to the required resources and content, and micro-segmentation for separating networks into smaller parts by minimizing the impact of a potential attack.
Network Perimeters: The architecture is capable of defining perimeters around parts of the networks where the most valuable assets are located while providing additional security mechanisms, such as encryption of data traffic and requests.
Cloud-based Workloads: Such workloads have the benefit of being tested through constant security routines for possible vulnerability reports, which is also related to the aspect of real-time monitoring. Thus, industry functionalities, virtual machines, and databases are protected through specifically designed solutions and access management, since they are linked to a public cloud.
Data: Zero trust architectures are defined by enhanced data security. Identifying sensitive data, monitoring data flow, and defining access prerequisites depending on data requirements are only a part of the essential protection strategies. As mentioned in the Zero Trust architecture, each protection mechanism can be implemented either on the whole industrial infrastructure or just the vital and valuable networks and databases.
Identity verification: The model performs constant monitoring of users during attempts to access data, achieving efficient detection of interference, reducing unnecessary access, and enabling instant protection against cyber-attacks.
Devices: User devices are stored in a thorough catalog. The enterprise is then capable of detecting, preventing, and responding to security threats of authorized devices, or recognizing malicious devices that are connected to the system for the first time.
Any implementation examples of the Zero Trust architecture?
There are many Zero Trust solutions available, for different types of scenarios.
One of the most popular implementation examples has been posted by Microsoft, focusing on the protection of its services and applications. Specifically, its design has been developed for the protection of devices running different types of operating systems, e.g., Windows, macOS, Android, or iOS, as well as performing a high-quality cloud-based device management service.
The corresponding model has four phases:
Identity verification: Currently, Microsoft utilizes a two-factor authentication system for access to their systems. Historically, initial access was achieved through a smartcard, which then evolved into a phone-based solution through the Azure Authentication app.
Device verification: Microsoft implements a type of prerequisite policy for devices before they are granted full access to its systems. They need to be fully healthy and free of viruses, malware software, or other vulnerabilities. In extreme cases where they need to support “unrecognized devices”, they provide virtual editions of software and applications.
Access verification: The company provides limited access to primary resources, which requires both identity and device verification. Moreover, there is implemented network protection by transitioning network access through the corporate network to normal internet access, in order to minimize unnecessary user access.
Service verification: It is considered a project under development, for healthy interaction between users and Microsoft’s applications. Just like the stages mentioned above, the company develops health testing strategies for its services, before the beginning of user access.
Another example of implementation is provided by Blackberry as to the proper steps that need to be taken for Zero Trust deployment.
Cataloging: Blackberry suggests that cataloging data, applications, and services should be an essential part of a Zero Trust model. Cataloging can also assist in the selection of proper data defense mechanisms.
Interconnection flow: Monitoring data flows and how they are interconnected with the rest of the components, transactions, and stakeholders, the company is able to recognize its valuable assets from its secondary resources, in relation to prioritizing security strategies.
Policy definition: Focusing on the stage of interconnection flows, the industry can design access streams, regarding the number of authorized users on specific databases, through specialized applications, as well as the types of authentications required.
Trial phases: This is also an experimentation process, in order to highlight vulnerabilities to the initial system. Usually, organizations perform the testing phases on infrastructure layers of lower importance or specialized virtual testbeds for advanced statistics and proposed changes.
Further development and updating: Depending on the results of the testing phase, further evaluation could be implemented before an official installation of the Zero Trust architecture. There are possibilities about replacing essential or secondary components, further enhancing existing ones, or completely removing them.
Conclusion
In this blog post, we thoroughly examined the architecture, principles, and implementation of a Zero Trust model.
One could assume that it is a strict and highly defensive concept since it treats any connected or cataloged device as a potential threat to the infrastructure and organization’s system. However, it is significantly adaptable according to the company’s needs, while providing solutions both as prevention and active defense.
Thus, paying attention to the current technological trends and potential upgradeability of such models can ensure fully functional protection with a minimal negative impact on a valuable corporation system.
